Cybersecurity Analyst Resume Examples

Mar 31, 2025
|
12 min read
Secure your career with a top-notch cybersecurity analyst resume. Start your journey to becoming the 'guardian of the net' by showcasing your skills, ensuring your profile locks in opportunities with the right keywords.
Rated by 348 people

Application Security Analyst

Information Systems Security Analyst

Digital Forensics Analyst
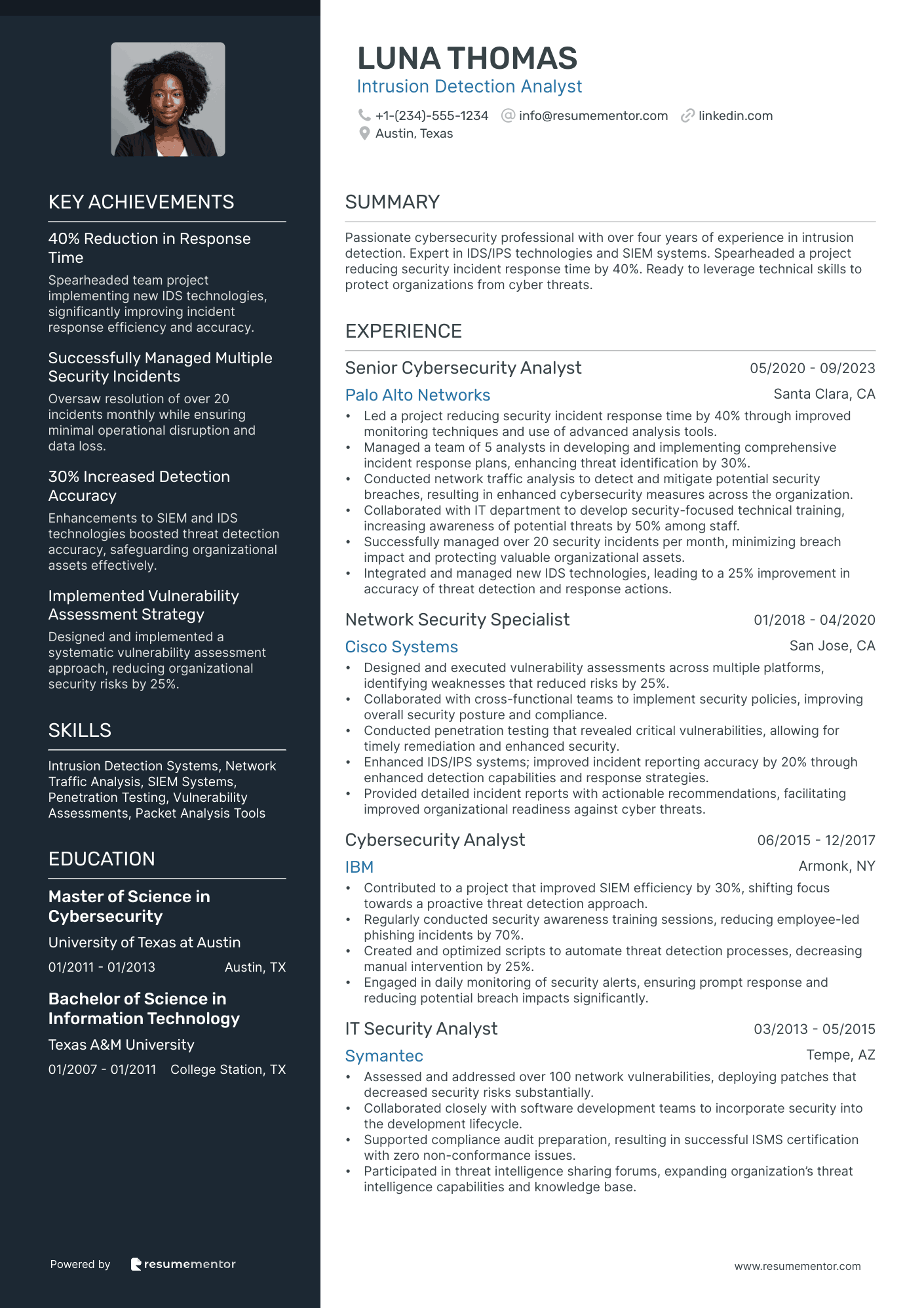
Intrusion Detection Analyst

Cyber Threat Intelligence Analyst

Data Protection Analyst

Penetration Tester

Industrial Control Systems Security Analyst

Application Security Analyst resume sample
- •Conducted over 100 vulnerability assessments annually, identifying critical security issues, resulting in a 20% reduction in security breaches.
- •Collaborated with the development team to integrate OWASP Top Ten standards into the SDLC, improving application security posture by 35%.
- •Performed penetration testing on web applications, uncovering serious vulnerabilities that led to increased security measures and user trust.
- •Developed comprehensive application security guidelines followed across the company, leading to enhanced secure coding practices.
- •Delivered secure coding workshops to over 50 developers quarterly, increasing awareness and adherence to security standards.
- •Participated in incident response team to address application security issues, reducing resolution time by 40% through effective troubleshooting.
- •Implemented dynamic analysis tools across 10 projects to streamline vulnerability scanning, resulting in a 25% reduction in unknown threats.
- •Analyzed and communicated vulnerabilities to diverse teams, successfully remediating 90% of high-risk security issues.
- •Initiated threat modeling exercises for 5 new applications, enhancing risk assessment and mitigation strategies significantly.
- •Kept abreast of emerging threats and security protocols, contributing to technical knowledge sharing and innovation.
- •Enhanced cloud security protocols, establishing secure practices for AWS environments, which led to a significant increase in data protection.
- •Provided expert guidance on compliance with PCI-DSS standards across multiple departments, achieving a 100% compliance rate.
- •Led secure software development lifecycle initiatives, embedding security into development processes and reducing vulnerabilities by 18%.
- •Facilitated interactive secure coding training sessions, enhancing developers' capabilities in identifying and mitigating potential threats.
- •Developed actionable security solutions tailored to specific organizational needs, resulting in improved security operations.
- •Monitored and assessed security systems, leading to swift identification and management of security incidents.
- •Increased security awareness by hosting training for teams, leading to a proactive approach in identifying risks.
- •Implemented a vulnerability management program, achieving a 50% reduction in system vulnerabilities.
- •Authored comprehensive security policies, aligning with ISO 27001 standards to support business needs.
Information Systems Security Analyst resume sample
- •Spearheaded the implementation of SIEM solutions, enhancing real-time monitoring which led to a 35% reduction in incident response times.
- •Designed comprehensive security policies and procedures, resulting in a 50% improvement in regulatory compliance audit scores.
- •Oversaw vulnerability assessment projects, identifying and mitigating over 400 security concerns to strengthen organizational defense.
- •Conducted risk assessments for critical infrastructures, reducing potential threats by 60% due to targeted mitigation actions.
- •Collaborated with cross-functional teams to align security measures with business objectives, improving stakeholder engagement by 25%.
- •Managed security incidents from detection through resolution, achieving an average closure time of 48 hours, cutting incident costs by 40%.
- •Led security awareness training programs, increasing employee engagement in security protocols by 30% over two years.
- •Monitored security logs and alerts with advanced SIEM tools, promptly addressing over 200 security alerts to protect data integrity.
- •Developed and enforced ISO 27001 aligned standards, improving compliance rates by almost 50% in annual assessments.
- •Collaborated in evaluating new security technologies, adopting three new tools that enhanced perimeter defenses by 40%.
- •Authored and maintained an incident log, ensuring comprehensive documentation and future audit readiness.
- •Conducted advanced penetration testing and security audits, identifying exploitable vulnerabilities, reducing incidents by 20%.
- •Recommended security toolsets that improved intrusion detection rates by 15%, maintaining robust defense mechanisms.
- •Trained junior IT staff on cybersecurity essentials, fostering a knowledgeable team and improving incident responses by 25%.
- •Assisted in GDPR compliance initiatives, contributing to successful data protection assessments reducing risk exposure.
- •Supported security infrastructure development, increasing system uptime by 10% due to proactive maintenance and monitoring.
- •Participated in cross-departmental collaboration to establish standardized security practices, achieving 95% compliance rate.
- •Identified and rapidly addressed malware threats, reducing malware impact durations by 40% within the organization.
- •Facilitated security incident documentation processes, enhancing post-incident learning and future preventative processes.
Digital Forensics Analyst resume sample
- •Led a forensic investigation solving a security breach that saved the company over $2 million in potential losses.
- •Implemented forensic methodologies that increased investigation efficiency by 25%, resulting in faster response times.
- •Collaborated with legal teams to prepare evidence, enhancing court case readiness by 30%, ensuring successful outcomes.
- •Trained junior analysts in best practices, contributing to a 15% improvement in team performance and skill development.
- •Orchestrated recovery of critical data from compromised systems, preventing loss of proprietary information.
- •Utilized EnCase and FTK tools to preserve digital artifacts, maintaining an impeccable chain of custody during investigations.
- •Conducted over 100 computer and mobile device investigations, increasing case resolution rates by 20%.
- •Developed and implemented incident response protocols for clients, enhancing response efficiency by 40%.
- •Provided expert testimony in high-profile cases, contributing significantly to the successful prosecution of cybercriminals.
- •Utilized X1 and EnCase to analyze network systems, uncovering unauthorized access and securing sensitive information.
- •Monitored cybersecurity trends, ensuring up-to-date threat intelligence and proactive risk mitigation for clients.
- •Performed forensic analysis for multiple Fortune 500 companies, identifying vulnerabilities and recommending actionable safeguards.
- •Recovered lost data for clients, preventing financial loss and preserving reputational integrity.
- •Collaborated closely with cybersecurity teams to devise robust strategies that reduced breach incidents by 35%.
- •Authored comprehensive forensic reports that were instrumental for legal teams in progressing litigation.
- •Strengthened system security with robust configurations, decreasing vulnerabilities by 50% across client networks.
- •Engaged in continuous system monitoring, flagging potential threats and reducing incident response time by 40%.
- •Collaborated with cross-functional teams to implement security measures, leading to a 30% decrease in security incidents.
- •Assisted in organizing and conducting client cybersecurity awareness workshops, improving client knowledge and practices.
Intrusion Detection Analyst resume sample
- •Led a project reducing security incident response time by 40% through improved monitoring techniques and use of advanced analysis tools.
- •Managed a team of 5 analysts in developing and implementing comprehensive incident response plans, enhancing threat identification by 30%.
- •Conducted network traffic analysis to detect and mitigate potential security breaches, resulting in enhanced cybersecurity measures across the organization.
- •Collaborated with IT department to develop security-focused technical training, increasing awareness of potential threats by 50% among staff.
- •Successfully managed over 20 security incidents per month, minimizing breach impact and protecting valuable organizational assets.
- •Integrated and managed new IDS technologies, leading to a 25% improvement in accuracy of threat detection and response actions.
- •Designed and executed vulnerability assessments across multiple platforms, identifying weaknesses that reduced risks by 25%.
- •Collaborated with cross-functional teams to implement security policies, improving overall security posture and compliance.
- •Conducted penetration testing that revealed critical vulnerabilities, allowing for timely remediation and enhanced security.
- •Enhanced IDS/IPS systems; improved incident reporting accuracy by 20% through enhanced detection capabilities and response strategies.
- •Provided detailed incident reports with actionable recommendations, facilitating improved organizational readiness against cyber threats.
- •Contributed to a project that improved SIEM efficiency by 30%, shifting focus towards a proactive threat detection approach.
- •Regularly conducted security awareness training sessions, reducing employee-led phishing incidents by 70%.
- •Created and optimized scripts to automate threat detection processes, decreasing manual intervention by 25%.
- •Engaged in daily monitoring of security alerts, ensuring prompt response and reducing potential breach impacts significantly.
- •Assessed and addressed over 100 network vulnerabilities, deploying patches that decreased security risks substantially.
- •Collaborated closely with software development teams to incorporate security into the development lifecycle.
- •Supported compliance audit preparation, resulting in successful ISMS certification with zero non-conformance issues.
- •Participated in threat intelligence sharing forums, expanding organization’s threat intelligence capabilities and knowledge base.
Cyber Threat Intelligence Analyst resume sample
- •Led proactive defense strategies resulting in a 25% decrease in successful phishing attacks over a 6-month period.
- •Monitored threat intelligence data from 5 diverse sources daily, successfully identifying a major ransomware threat.
- •Developed and shared over 15 comprehensive threat intelligence reports, enhancing the security posture of multiple departments.
- •Improved threat intelligence tools accuracy across systems, boosting efficiency by 20% within the first quarter.
- •Collaborated with internal teams, optimizing incident response plans, which led to a 30% faster incident resolution time.
- •Trained 50 staff members on cybersecurity awareness, significantly decreasing susceptibility to social engineering attacks.
- •Performed in-depth malware analysis, identifying and neutralizing three new malware strains, reducing threat risks by 40%.
- •Spearheaded continuous updates to threat intelligence platforms, increasing system accuracy and data currency.
- •Facilitated the creation of threat intelligence dashboards, providing insights into emerging cyber threats to technical teams.
- •Managed and analyzed over 100 daily threat alerts, successfully prioritizing and mitigating potential risks.
- •Collaborated with cross-functional teams, enhancing cybersecurity protocols, which resulted in a 50% decrease in incident response time.
- •Developed key threat management strategies leading to a 30% improvement in overall security incident management.
- •Monitored SIEM platforms, analyzing data and safeguarding network integrity from potential threats and breaches.
- •Generated incident reports used in strategic decisions to enhance defensive technologies and policies.
- •Devised system protocols improving threat detection speed by 25%.
- •Advised on security architecture, helping clients enhance systems that led to a 15% reduction in vulnerability exposure.
- •Conducted comprehensive security assessments, pinpointing key weaknesses in client infrastructure networks.
- •Assisted in incident response drills, increasing team effectiveness and readiness by 40%.
- •Implemented new security regulations for clients, achieving compliance in 6 related cases.
Data Protection Analyst resume sample
- •Led a cross-departmental team to implement new GDPR compliance measures, improving data handling efficiency by 25% over a 12-month period.
- •Conducted over 50 data protection impact assessments annually, resulting in a 30% reduction in compliance-related incidents.
- •Collaborated with IT and legal teams to develop comprehensive data protection training, enhancing staff awareness and decreasing data breaches by 40%.
- •Spearheaded the response to DSARs, improving average response times to under 15 days and increasing overall customer satisfaction by 15%.
- •Established and maintained records of processing activities, ensuring full compliance and aligning with industry best practices.
- •Provided expert guidance on data privacy issues, successfully minimizing regulatory risks and demonstrating leadership in privacy-first initiatives.
- •Advised Fortune 500 clients on GDPR and CCPA compliance, contributing to improved data handling strategies and regulatory adherence.
- •Coordinated audits that identified and mitigated potential risks, reducing non-compliance penalties by 35% within the first year.
- •Developed and implemented new data protection policies, which were adopted by 100% of client departments leading to increased operational compliance.
- •Conducted quarterly training for over 200 employees, enhancing their understanding of data protection responsibilities and reducing errors by 20%.
- •Monitored data protection compliance across multiple sectors, providing actionable insights and ensuring continuous improvement across all channels.
- •Managed data privacy initiatives for high-profile clients, increasing regulatory adherence and securing data assets more effectively.
- •Assisted in deploying data management tools, which enhanced data accuracy and streamlined data processing activities by 22%.
- •Guided junior analysts in interpreting data legislation, fostering a knowledgeable team that strengthened organizational data security.
- •Managed complex data subject access requests, improving processing efficiency and maintaining compliance benchmarks effectively.
- •Executed compliance audits for financial services clients, achieving a 15% increase in audit completion rates.
- •Balanced multiple compliance projects simultaneously, ensuring adherence to evolving data protection regulations and internal policies.
- •Introduced a new tracking system that reduced compliance issue resolution times by 20%, enhancing overall operational efficiency.
- •Provided analysis and insights on legislative updates, proactively adjusting policies to mitigate risk and enhance data protection efforts.
Penetration Tester resume sample
- •Led comprehensive penetration testing projects, identifying vulnerabilities in over 50 client systems quarterly, enhancing security protocols by 40%.
- •Collaborated with cross-functional teams to develop effective remediation strategies, resulting in a 30% decrease in system vulnerabilities.
- •Coordinated and facilitated workshops to train 15 junior staff on advanced penetration testing techniques, fostering professional growth.
- •Executed thorough vulnerability assessments, producing detailed reports that influenced strategic security decisions for clients.
- •Implemented security testing methodologies, ensuring adherence to compliance standards such as OWASP, which led to increased client satisfaction.
- •Developed custom testing scripts that improved test coverage by 25% while also saving 15% on testing time.
- •Conducted security audits on web applications, reducing identified risks by 45% through immediate corrective actions.
- •Streamlined pentesting processes, enhancing speed and precision by implementing innovative test automation techniques.
- •Consulted with 10+ clients quarterly, providing insight into protecting against emerging cybersecurity threats.
- •Achieved a 70% client retention rate through excellent service and delivery, leading to significant revenue growth.
- •Engaged in security breach simulations, improving organizational resilience and preparedness by 50%.
- •Monitored and analyzed network traffic, proactively preventing potential breaches through real-time alerts and responses.
- •Developed security policies and procedures which reduced successful intrusion attempts by 20%.
- •Authored technical documentation on cybersecurity protocols which became reference material for 5 departments.
- •Performed daily threat analysis, offering timely solutions that improved threat response efficiency by 30%.
- •Managed firewall and antivirus systems, ensuring network security compliance and reducing malware incidents by 30%.
- •Conducted vulnerability scans and advised system upgrades, leading to an 18% increase in network stability.
- •Collaborated on international project teams to secure client networks against advanced persistent threats.
Industrial Control Systems Security Analyst resume sample
- •Led a team to implement security patches across a large ICS environment, reducing vulnerabilities by 40%.
- •Conducted comprehensive risk assessments leading to a 25% decrease in potential cyber threats to critical systems.
- •Collaborated with cross-functional teams to develop and deploy a new incident response strategy, reducing response time by 30%.
- •Developed security policies aligned with ISA/IEC 62443 standards, resulting in improved compliance and enhanced security framework.
- •Provided advanced training sessions on incident management for staff, increasing awareness and readiness by 50%.
- •Utilized SIEM tools to monitor and detect anomalies, achieving a 20% increase in threat detection rates.
- •Managed and improved the security architecture for multiple ICS projects, leading to a 35% reduction in unauthorized access.
- •Implemented a proactive threat monitoring program that reduced incident occurrences by 18%.
- •Participated in internal audits ensuring 100% compliance with NERC CIP standards across operational sites.
- •Designed and executed vulnerability testing on control systems, reducing potential exploits by 22%.
- •Collaborated with IT teams to integrate cross-platform security solutions, achieving a seamless protection strategy across networks.
- •Engineered network security solutions that safeguarded ICS platforms, leading to a 15% increase in network resilience.
- •Conducted risk assessments on network protocols, resulting in enhanced secure communications and 20% less data breach risk.
- •Implemented firewall solutions and hardening protocols that improved system security efficacy by 28%.
- •Facilitated inter-departmental workshops, fostering a shared understanding of cybersecurity needs and strategies.
- •Provided consultancy to optimize security for 20+ industrial networks, achieving improved protection against cyber threats.
- •Evaluated and recommended security tools that enhanced assessment capabilities and improved overall system security by 10%.
- •Trained personnel on best practices in cybersecurity, resulting in a 25% improvement in security awareness.
- •Monitored and responded to security incidents, ensuring timely reporting and resolution to safeguard critical infrastructure.
As a cybersecurity analyst, think of your resume as your virtual firewall, standing firm between you and potential employers. Crafting this crucial document can be as challenging as tracking down a digital intruder. You need to highlight your technical expertise in a way that resonates with the industry.
Your task is to clearly communicate your skills in threat analysis, risk assessment, and intrusion detection. This involves the same careful construction you use to patch vulnerabilities in a network. Describing your experience, certifications, and achievements can often feel overwhelming, but it’s essential to convey your value.
To streamline this process, consider using a structured resume template. An organized template allows you to focus on what matters most, like specific security frameworks you’ve worked with and the incidents you’ve expertly resolved. The right framework can make your qualifications stand out.
Embarking on the journey from job seeker to vital team member begins with a resume that truly reflects your worth. By tailoring it to showcase both your technical abilities and your soft skills, you can confidently move towards your next career milestone. Remember, your cybersecurity skills safeguard digital landscapes; now, let your resume protect your career path with the same diligence.
Key Takeaways
- Crafting a cybersecurity analyst resume involves clearly communicating your skills in threat analysis, risk assessment, and intrusion detection while showcasing your experience, certifications, and achievements.
- An organized resume template can streamline the process, allowing focus on specific security frameworks and incidents you've resolved, making your qualifications stand out.
- The reverse-chronological format is recommended, and modern fonts enhance readability and professionalism in the tech industry.
- An impactful experience section should include measurable achievements, collaboration, innovation, and roles where responsibilities have driven security improvements.
- Highlight relevant certifications, education, skills, and additional sections like languages and volunteer work to enhance personal touches and industry alignment.
What to focus on when writing your cybersecurity analyst resume
A cybersecurity analyst resume should clearly convey your expertise in protecting information systems and preventing cyber threats. You want to highlight both your skills in security protocols and your ability to assess risk effectively, while also showcasing your technical knowledge and adaptability in a fast-evolving industry.
How to structure your cybersecurity analyst resume
- Contact Information: Make sure your full name, phone number, email address, and LinkedIn profile are included—this information should be at the top of your resume, reflecting a professional image and ensuring you're easily reachable by potential employers.
- Professional Summary: Provide a snapshot of your experience and key accomplishments in cybersecurity—craft this section as a compelling introduction that grabs attention by using keywords like "threat assessment" and "network security," summarizing what makes you a strong candidate.
- Work Experience: When listing your previous cybersecurity roles, include company names, dates, and key responsibilities—focus on experiences where you implemented security measures or dealt with security incidents, connecting your past successes to your future potential and demonstrating your proven track record.
- Technical Skills: It’s crucial to specify the cybersecurity tools, programming languages, and systems you know well—emphasize your proficiency in using SIEM technologies, Python, or firewall configurations, linking your hands-on skills to industry needs and showing your technical versatility.
- Certifications: Listing relevant certifications like CISSP, CEH, or CompTIA Security+ highlights your expertise—these credentials underscore your commitment to ongoing education and reinforce your knowledge base, which is essential in the ever-evolving field of cybersecurity.
- Education: Detail the educational background that supports your career, including any relevant coursework or projects—your academic achievements should align with your professional goals, providing a solid foundation for your expertise in the cybersecurity domain.
Before you move on to structuring your resume, remember that the format is just as important as the content—in the sections below, we'll cover each component in more depth, ensuring your resume is comprehensive and effective.
Which resume format to choose
As a cybersecurity analyst, selecting the optimal resume format can greatly impact how effectively your qualifications are communicated. The reverse-chronological format is the most suitable for this role because it allows you to prominently feature your recent and relevant experiences. This approach is widely accepted in the tech industry and helps potential employers quickly understand your skills and career progression, which is essential for roles requiring rapid adaptation to evolving cyber threats.
Choosing the right font further enhances the modern and professional look of your resume. Opt for contemporary fonts like Rubik, Lato, or Montserrat, which are not only aesthetically pleasing but also enhance readability. These fonts align with the tech-savvy nature of a cybersecurity analyst role, subtly emphasizing your fit in the cutting-edge tech world without overshadowing your content.
Ensuring that your resume is saved as a PDF is crucial. This format preserves your layout and content across all digital platforms, regardless of the recipient’s device or software. In a field where precision and attention to detail are key, a well-presented PDF resume reflects professionalism and a command of technology, vital traits for successful cybersecurity analysts.
Setting your margins between 0.5 and 1 inch is a small but significant detail. Proper spacing ensures your content appears organized and accessible, making it easier for hiring managers to follow the narrative of your experiences and skills. This attention to layout detail mirrors the precision required in cybersecurity tasks, where even minor elements can make a significant difference.
Each of these considerations—format, font, file type, and layout—work together to create a cohesive and professional resume. They help you present yourself as a competent and methodical candidate, ready to tackle the complexities of the cybersecurity sector.
How to write a quantifiable resume experience section
To create a compelling cybersecurity analyst experience section, focus on highlighting tangible achievements and relevant metrics to show employers how effectively you've applied your skills. Organize it in reverse chronological order, beginning with your most recent role, and include experience from the last 10-15 years or positions directly relevant to cybersecurity. Tailor each entry by integrating keywords from the job description, and employ strong action verbs like "implemented," "analyzed," and "secured" to clearly illustrate your contributions.
- •Reduced potential cyber threats by 40% through advanced threat modeling and risk assessments.
- •Built a security awareness program, boosting employee compliance with protocols by 30%.
- •Managed and secured a network of over 500 devices, achieving zero incidents over two years.
- •Improved incident response speed, cutting the average response time from 5 hours to 1 hour.
This experience section stands out because it seamlessly integrates measurable achievements with strong action verbs, illustrating your effectiveness in cybersecurity. By focusing on results like reducing potential threats by 40% and improving response times, you vividly demonstrate your impact. Action verbs like "reduced," "built," and "managed" not only convey initiative but also connect each sentence naturally, highlighting both your leadership and technical capabilities. This approach aligns your skills and accomplishments with what employers are actively seeking, creating a cohesive and impressive narrative.
Collaboration-Focused resume experience section
A collaboration-focused cybersecurity analyst resume experience section should clearly demonstrate your ability to work effectively with others to reach common goals. Start by selecting experiences where teamwork made a significant impact. Use dynamic language to describe how you joined forces with colleagues to meet objectives and overcome challenges. Go beyond merely listing duties; illustrate how your collaborative efforts brought tangible benefits to the team and organization.
Enhancing your achievements with numbers can add clarity. For instance, if you developed a security protocol as part of a team, explain the outcome, such as increased efficiency. Include any specific tools or methods that contributed to successful collaborations. The goal is to showcase your aptitude for working with others to drive positive, measurable results.
Cybersecurity Analyst
Tech Solutions Inc.
March 2020 - Present
- Worked with IT and development teams to implement a firewall, reducing potential threats by 30%.
- Led a team of analysts to design a threat detection system, boosting response time by 15%.
- Collaborated with cross-functional teams to develop security training, decreasing phishing incidents by 25%.
- Facilitated weekly meetings with technical and non-technical teams to ensure a 95% compliance rate.
Innovation-Focused resume experience section
An innovation-focused cybersecurity analyst resume experience section should emphasize your creative problem-solving skills and your ability to tackle challenges with new approaches. Begin by clearly stating your role, the company you worked for, and the duration of your employment. Focus on the innovative projects you've led, explaining how your resourceful solutions made a difference. In the bullet points, detail your accomplishments, highlighting actions that showcase your ability to think outside the box and improve security measures. Numbers and measurable outcomes provide solid proof of your impact, so include them whenever possible.
Ensure your writing is clear and concise, making your resume easy to read. Mention any new processes you initiated or how you creatively safeguarded systems against threats. By maintaining a positive tone, you can illustrate the meaningful contributions you made within the organization. Tie your experiences together by showing how your innovation in cybersecurity reflects your adaptability and foresight. Share examples of how you've proactively protected data and refined system protocols, demonstrating a proactive approach in addressing potential threats.
Cybersecurity Analyst
TechGuard Solutions
January 2020 - Present
- Developed an adaptive threat detection system, cutting security incidents by 30%.
- Introduced AI-driven tools, boosting threat response time by 25%.
- Worked with different teams to design a new incident report protocol, increasing team efficiency.
- Led efforts to spot and fix software vulnerabilities, preventing data breaches.
Responsibility-Focused resume experience section
A responsibility-focused cybersecurity analyst resume experience section should clearly articulate your daily tasks and the impact you've had through them. Start by using action verbs like "monitored," "analyzed," and "improved" to describe your contributions effectively. These verbs help paint a picture of your proactive approach to maintaining security. It's essential to highlight how your responsibilities have benefited your previous employers, focusing on the challenges you addressed and the innovative solutions you implemented.
When crafting this section, begin by noting the dates of your employment, followed by your job title and workplace name. Use bullet points to succinctly convey your key achievements and responsibilities, showcasing how you've bolstered security measures or optimized processes. Including numbers or tangible outcomes whenever possible will enhance the credibility and impact of your statements. This strategy enables potential employers to quickly see the unique value you've brought in past roles, ensuring the experience section remains concise yet highly effective. Tailoring your examples to fit the role you're applying for can further enhance the relevance and appeal of your resume.
Cybersecurity Analyst
Tech Innovations Corp
January 2020 - Present
- Monitored network traffic to identify and respond to suspected security incidents, decreasing response time by 40%
- Conducted regular vulnerability assessments, resulting in a 25% reduction in security threats over a year
- Developed a security awareness program that increased employee participation by 60%
- Collaborated with IT teams to strengthen firewall rules, enhancing network security by preventing unauthorized access
Efficiency-Focused resume experience section
A cybersecurity analyst efficiency-focused resume experience section should emphasize simplicity and make a strong impact by highlighting your ability to enhance processes. Start by listing your job titles, places of employment, and the dates of your tenure. Use bullet points to detail your specific accomplishments and actions, ensuring you provide enough detail to give a clear picture of your contributions.
You should focus on measurable outcomes like cutting down incident response times or improving threat detection accuracy. Including numbers and percentages can give weight to these achievements and help potential employers understand your real-world impact. For those just starting out or with fewer quantifiable results, it's beneficial to highlight projects where you introduced new processes or tools, showcasing improvements in team or individual performance.
Cybersecurity Analyst
Tech Solutions Inc.
2020-Present
- Reduced average incident response time by 35% through process optimization.
- Developed and implemented a training program leading to a 40% improvement in recognizing phishing attempts.
- Streamlined threat analysis by integrating automated tools, reducing manual effort by 30%.
- Collaborated with cross-functional teams to enhance system security, achieving a 25% decrease in vulnerability incidents.
Write your cybersecurity analyst resume summary section
A cybersecurity-focused resume summary section should grab an employer’s attention immediately. Begin by introducing yourself with confidence, highlighting your most impressive skills and experiences in just a few sentences. This introduction sets the stage for a compelling first impression. Use active language to showcase your strengths and the impact you’ve made in past roles, demonstrating precisely why you’re the ideal candidate for the job. The concise presentation of your achievements is crucial in quickly conveying your value.
This summary effectively highlights specific achievements and clarifies your expertise. Be sure to use numbers to add weight to your claims, as quantifying success makes a stronger impact. A resume summary is different from a resume objective; while the summary focuses on past accomplishments, the objective looks ahead to future goals. In contrast, a resume profile offers a broader overview of who you are, and a summary of qualifications presents key skills succinctly. Tailor your summary to the job, aligning your past achievements with the role’s needs. This approach will make your application stand out in the competitive field of cybersecurity.
Listing your cybersecurity analyst skills on your resume
A cybersecurity-focused resume should skillfully showcase your abilities, whether you choose to highlight them in a standalone skills section or integrate them throughout your experience and summary. By keeping a standalone section, your skills are easily visible to both hiring managers and digital systems that scan resumes. If you weave them into other parts of your resume, it demonstrates how you've applied these skills effectively in past roles.
Your strengths and soft skills are like your unique tools that reveal your personality and teamwork capabilities. While soft skills focus on how well you communicate and solve problems, hard skills are the technical bricks and mortar of your expertise, like specific cybersecurity tools or coding languages you've mastered. When these skills are also used as resume keywords, it amplifies your chances with automated systems that many companies use to find top talent.
Aligning your skills with resume keywords ensures that your profile warms up to what employers are actively looking for. Below is an example of a powerful skills section, designed to catch attention:
This particular section is direct and focused, highlighting critical skills essential for cybersecurity roles. With each skill outlined clearly, it paints a vivid picture of your technical capabilities in safeguarding digital landscapes.
Best hard skills to feature on your cybersecurity analyst resume
Cybersecurity analysts need hard skills that demonstrate their tech-savvy nature and readiness to fend off threats. These skills signal to employers that you can secure their systems effectively. Here’s a comprehensive list of in-demand hard skills:
Hard Skills
- Network Security
- Threat Analysis
- Incident Response
- Risk Assessment
- Vulnerability Management
- Firewall Management
- Data Encryption
- Penetration Testing
- Security Information and Event Management (SIEM)
- Malware Analysis
- Intrusion Detection Systems (IDS)
- Cloud Security
- Secure Coding
- Cybersecurity Frameworks (e.g., NIST, ISO)
- Identity and Access Management (IAM)
Best soft skills to feature on your cybersecurity analyst resume
In the world of cybersecurity, soft skills are just as crucial. They highlight your ability to collaborate, tackle challenges, and adapt to new situations, showing potential employers how well you'll integrate into their teams. Here are fifteen valuable soft skills:
Soft Skills
- Communication
- Critical Thinking
- Attention to Detail
- Problem Solving
- Adaptability
- Teamwork
- Time Management
- Initiative
- Patience
- Stress Management
- Empathy
- Creativity
- Leadership
- Collaboration
- Conflict Resolution
How to include your education on your resume
The education section is an important part of your cybersecurity analyst resume, as it showcases your formal training and academic credentials. Make sure to tailor this section specifically to the job you're applying for, emphasizing relevant qualifications and omitting unrelated education. Include your school name, degree, and the time you attended. List any honors such as cum laude right after your degree to highlight your academic achievements. If your GPA is above 3.5, you can proudly display it on your resume. Be careful to list your degree clearly to ensure that potential employers understand your qualifications.
Incorrect example:
This is not relevant for a cybersecurity analyst.
Correct example:
This example is effective because it highlights a relevant degree, includes a strong GPA, and lists academic honors, providing a clear signal to employers of your dedication and expertise.
How to include cybersecurity analyst certificates on your resume
In the world of cybersecurity, highlighting your certifications is crucial. Certifications validate your expertise and can tilt the scales in your favor for potential employers. List the name of each certificate clearly. Include the date when you earned it to show your recent efforts in skill enhancement. Add the issuing organization to bolster credibility and provide context. You can also place your certificates in the header for quick visibility. For example, "Certified Ethical Hacker (CEH) - EC-Council, 2021" stands out and sets the tone for the rest of your resume.
Here is a good example of a standalone certificates section structured effectively:
This example works well because it includes certificates that are directly related to cybersecurity. Each certificate is clearly named, showcasing distinct skills. The inclusion of the issuing organizations gives credibility. Certifications like CISSP and CEH underscore technical proficiency, while Security+ shows a foundational understanding of security concepts. This thoughtful presentation speaks directly to a potential employer about your qualifications in the cybersecurity field.
Extra sections to include on your cybersecurity analyst resume
Crafting a resume as a cybersecurity analyst requires showcasing critical skills and experiences that align with industry demands. However, adding personal touches can set you apart in a sea of similar candidates.
Language section — Highlight any foreign languages you speak to show analytical advantages and cultural insights. Include brief details on your proficiency levels to emphasize the extent of your linguistic abilities.
Hobbies and interests section — Display your curiosity and personal skills by mentioning hobbies related to technology and problem-solving. Choose interests that reflect qualities desirable in the cybersecurity field, like attention to detail and persistence.
Volunteer work section — Demonstrate commitment to community and team skills by detailing relevant volunteer experiences. Focus on volunteer roles that enhanced your cybersecurity skills or involved tech-based projects.
Books section — Showcase your passion for learning and staying updated by listing influential cybersecurity or tech books you've read. Mention recent publications to illustrate commitment to keeping up with industry trends.
In Conclusion
In conclusion, crafting a resume as a cybersecurity analyst requires precision, much like protecting a digital network. Your resume is your virtual firewall, representing your skills and experiences to potential employers. It's essential to clearly showcase your expertise in threat analysis, risk assessment, and intrusion detection. Use a structured template to focus on your significant achievements and technical skills, enhancing your abilities in industry-relevant security frameworks.
Select a reverse-chronological format to highlight your most recent and relevant experiences, ensuring your career progression is clear. The integration of contemporary fonts and a PDF format ensures a modern, professional presentation. As you write, quantify your experiences with tangible achievements to demonstrate your effectiveness. This approach aligns with the industry’s demand for precise and actionable skill presentation.
Additionally, emphasize your skills in both a dedicated skills section and throughout your experience narratives. This method effectively communicates your technical expertise and adaptability. Consider extra sections, such as languages or volunteer work, to paint a fuller picture of your character and dedication. Tailor your resume to meet specific job requirements, ensuring your application is not only comprehensive but also closely aligned with what employers seek.
Remember, a well-crafted resume reflects your ability to safeguard digital environments, just as it secures your career path. By presenting yourself as a technically skilled and adaptable candidate, you enhance your prospects in the competitive field of cybersecurity. This diligence in constructing your professional story positions you for the next step in your career journey as a trusted guardian of digital landscapes.
Related Articles

Continue Reading
Check more recommended readings to get the job of your dreams.
Resume
Resources
Tools
© 2026. All rights reserved.
Made with love by people who care.

