Information Security Analyst Resume Examples

Mar 26, 2025
|
12 min read
Craft your information security analyst resume with these key tips to unlock your career potential. Shape your professional story while keeping unwanted errors at bay, and watch your job prospects soar into secure domains.
Rated by 348 people
Network Security Analyst

Cybersecurity Risk Analyst
Incident Response Analyst

Cloud Security Analyst
Information Security Compliance Specialist
Data Privacy Analyst
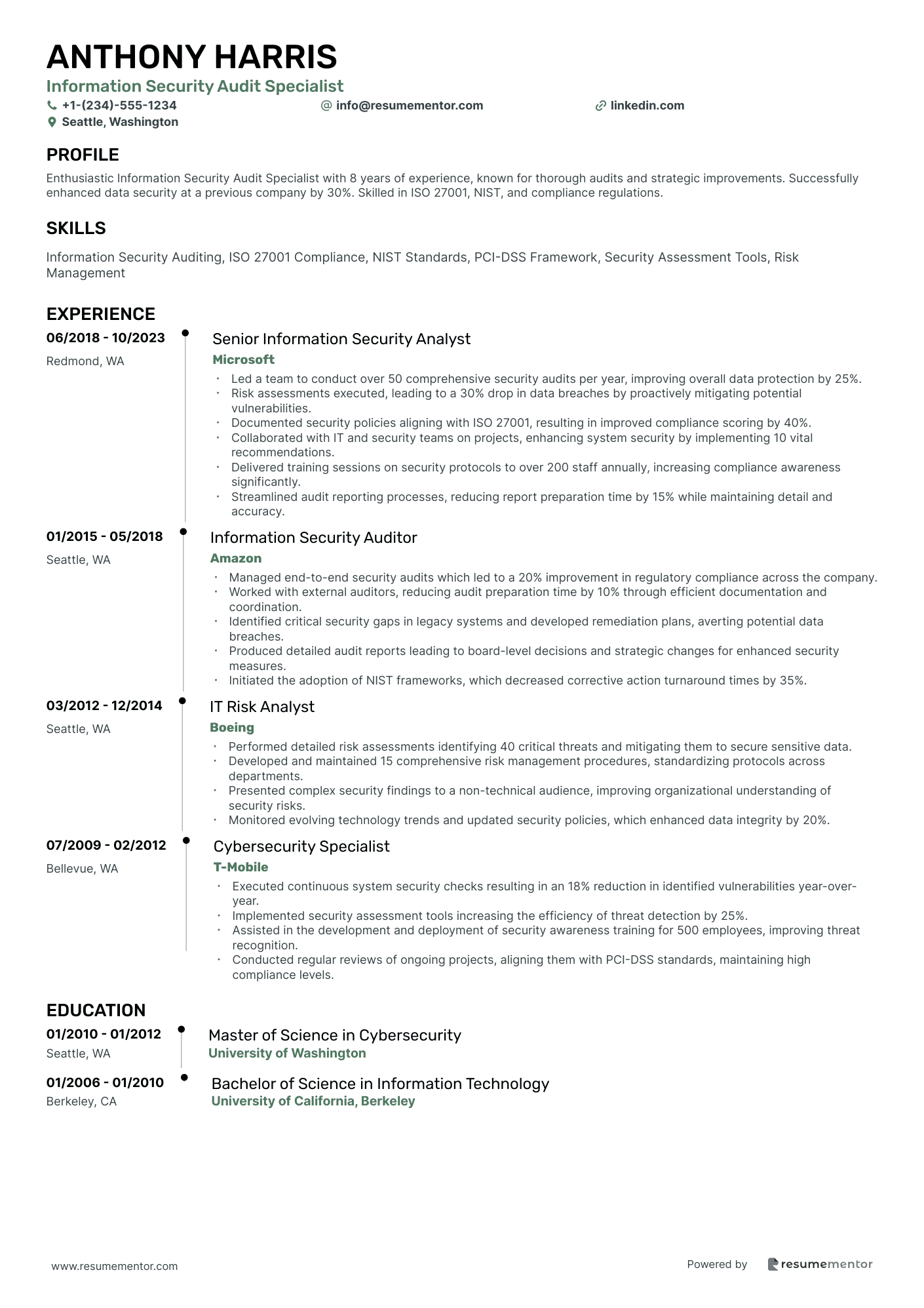
Information Security Audit Specialist

Information System Forensic Analyst

Information Security Vulnerability Assessor

Network Security Analyst resume sample
- •Enhanced network security protocols, reducing security incidents by 35% through strategic deployment of IDS and real-time analytics.
- •Implemented penetration testing processes that identified and mitigated critical vulnerabilities, resulting in strengthened data protection for a client base exceeding 2,000 users.
- •Monitored and analyzed network traffic, resulting in a 40% reduction in intrusion attempts by optimizing firewall settings and deploying advanced threat detection software.
- •Collaborated with cross-functional teams to design secure network architectures ensuring 99.9% uptime and system reliability.
- •Developed comprehensive security documentation and incident reports, improving incident response time by 25%.
- •Initiated a cybersecurity awareness program, increasing employee compliance with security protocols by 50%.
- •Conducted extensive vulnerability assessments, identifying over 150 security gaps and advancing remediation protocols to reduce risk exposure by 20%.
- •Engineered secure network configurations for firewalls, ensuring compliance with ISO 27001 standards and reducing unauthorized access attempts.
- •Played an instrumental role in constructing security policies and protocols, increasing overall network resilience and threat defense posture.
- •Responded rapidly to security breaches, executing root cause analysis and recommending corrective actions, reducing mean time to recovery by 30%.
- •Devised robust security architecture solutions, incorporating VPNs and advanced encryption measures, resulting in zero data breaches over two years.
- •Managed deployment and configuration of enterprise-level security tools, leading to improved network security by 25%.
- •Conducted security audits and system hardening across 100+ servers, reducing vulnerabilities and strengthening access controls.
- •Designed incident response plans, bolstering investigative capabilities and reducing breach detection time significantly.
- •Collaborated with software development teams to integrate security measures early in the design phase, preventing potential vulnerabilities.
- •Developed network monitoring solutions that enhanced threat detection capabilities, resulting in proactive remediation of attacks.
- •Utilized advanced analytics to track network anomalies and recommend actionable changes, reducing unauthorized access incidents by 40%.
- •Assisted in the implementation of robust firewall and router configurations, ensuring alignment with CIS Controls.
- •Maintained ongoing review and improvement of security documentation, ensuring up-to-date compliance with industry best practices.
Cybersecurity Risk Analyst resume sample
- •Conducted an extensive risk assessment program that identified over 120 vulnerabilities, enabling the implementation of critical security controls across the organization.
- •Developed and enforced new cybersecurity policies, reducing overall risk exposure by 45% within one year.
- •Collaborated with compliance teams to ensure the company’s information assets adhere to ISO 27001 standards, resulting in successful certification.
- •Orchestrated cross-department workshops raising cybersecurity awareness, contributing to a 30% decrease in phishing incidents reported by employees.
- •Implemented a Security Information and Event Management (SIEM) system, improving threat detection capabilities and response times by 25%.
- •Generated comprehensive risk assessment reports for executive management, providing insights and actionable recommendations that influenced strategic decisions.
- •Spearheaded vulnerability management initiatives, reducing identified system vulnerabilities by 40% over six months.
- •Worked with IT teams to implement enhanced security protocols that lowered threat occurrences by 28%.
- •Conducted cybersecurity risk training sessions for 200 employees, significantly improving cybersecurity practices within the organization.
- •Led post-incident analysis for major security events, contributing to improved response strategies and protocols.
- •Enhanced threat intelligence processes by integrating advanced monitoring tools, increasing the organization’s threat detection rate by 33%.
- •Implemented risk management strategies that aligned with NIST frameworks, reducing potential vulnerabilities by 25%.
- •Developed a robust incident response plan for the company, significantly enhancing security posture.
- •Supported implementation of a vulnerability scanner tool, detecting and resolving issues promptly and efficiently.
- •Produced technical reports for non-technical stakeholders, clearly communicating risk levels and recommendations.
- •Assisted in the deployment of advanced cybersecurity tools, enhancing the organization's threat detection capabilities.
- •Monitored network activity using security tools, contributing to a secure IT infrastructure.
- •Analyzed and documented risks associated with new IT initiatives, supporting informed business decisions.
- •Facilitated cross-functional security initiatives, improving interdepartmental communication and cooperation.
Incident Response Analyst resume sample
- •Monitored security alerts using SIEM tools, reducing false positives by 25% through rule refinement and proactive threat hunting.
- •Investigated an average of 50 security incidents monthly, accelerating response time by 30% through streamlined procedures.
- •Developed response plans for high-profile threats, enhancing security posture and reducing critical incident impact by 40%.
- •Conducted post-incident analysis, resulting in a 20% improvement in our threat detection capabilities.
- •Collaborated with IT teams to facilitate quick recovery from incidents, minimizing downtime from hours to minutes.
- •Delivered training programs on incident response, increasing team readiness and responsiveness by 35%.
- •Managed 24/7 security operations, analyzing over 1,000 alerts weekly and escalating critical incidents efficiently.
- •Conducted root cause analysis on major security breaches, leading to the development of more effective mitigation strategies.
- •Integrated new SIEM tools into existing frameworks, increasing log processing efficiency by 50%.
- •Coordinated with cross-functional teams to enhance real-time incident resolution, reducing average resolution time by 20%.
- •Prepared detailed incident reports for executive review, improving transparency and understanding of security threats.
- •Implemented new firewall configurations, decreasing unauthorized access attempts by over 45% within the first quarter.
- •Monitored and performed proactive threat assessments, increasing early threat detection rates by 30%.
- •Contributed to a 15-member team in completing a comprehensive security audit, identifying critical areas for process improvement.
- •Designed incident response protocols, standardizing procedures and reducing confusion in high-pressure situations.
- •Assisted in the deployment and maintenance of intrusion detection systems, enhancing network security by 35%.
- •Analyzed network traffic patterns, optimizing bandwidth usage and reducing unnecessary network congestion.
- •Supported regulatory compliance efforts, improving alignment with ISO 27001 standards across the organization.
- •Maintained detailed documentation of network vulnerabilities, aiding in the prioritization and resolution of incidents.
Cloud Security Analyst resume sample
- •Developed and implemented advanced security strategies, resulting in a 30% reduction in security incidents within the cloud environment.
- •Led comprehensive vulnerability assessments for over 100 cloud-based applications, substantially enhancing security posture.
- •Coordinated with cross-functional teams to implement security measures, which improved compliance with industry standards by 25%.
- •Integrated security solutions into CI/CD pipelines, decreasing code vulnerabilities by 40% and enhancing overall application resilience.
- •Managed real-time monitoring of cloud environments, promptly responding to breaches and reinforcing security protocols across platforms.
- •Presented security reports and insights to senior management, driving strategic decisions and investments in cybersecurity initiatives.
- •Implemented comprehensive threat modeling, enhancing risk mitigation strategies and reducing breach impact by 15%.
- •Monitored security alerts and logs, effectively resolving 90% of incidents within 24 hours to maintain data integrity.
- •Collaborated with DevOps to integrate security practices, increasing secure coding efficiency by 20%.
- •Conducted security workshops, raising organizational security awareness and decreasing non-compliance incidents by 30%.
- •Revamped security policies to align with NIST standards, fortifying system defenses and safeguarding sensitive information.
- •Executed regular security assessments, identifying 300+ vulnerabilities and spearheading remediation efforts.
- •Streamlined cloud security processes, achieving a 25% increase in efficiency and enhancing response times significantly.
- •Engineered automated scripts using Python, improving security analysis accuracy by 35% and reducing manual errors.
- •Provided expert security recommendations adopted across multiple teams, bolstering system defenses substantially.
- •Conducted detailed cloud security audits, leading to a 20% improvement in security controls.
- •Implemented security protocols adhering to ISO 27001 standards, enhancing compliance across cloud platforms.
- •Managed security tools including SIEM solutions, resulting in improved threat detection and faster incident response.
- •Collaborated with stakeholder teams to develop security solutions preventing potential data breaches effectively.
Information Security Compliance Specialist resume sample
- •Led a team in implementing security frameworks resulting in a 30% reduction in security incidents within one year.
- •Developed comprehensive security policies that improved compliance scores by 20%, aligning with ISO 27001 standards.
- •Conducted over 15 risk assessments annually, identifying critical vulnerabilities and resulting in $100K savings from potential breaches.
- •Collaborated with cross-functional teams to integrate security measures into 10 major IT projects, ensuring compliance with corporate and regulatory standards.
- •Monitored regulatory trends and provided training to ensure organizational preparedness for industry changes, affecting 500+ employees.
- •Presented quarterly reports to senior management on compliance initiatives, achieving positive feedback on information security enhancements.
- •Enhanced data security protocols across various departments, which resulted in a 40% increase in system security performance.
- •Assisted with a GDPR compliance project that improved company data protection ratings, facilitating European market expansion.
- •Orchestrated external compliance audits with no major findings and improved audit preparation processes company-wide.
- •Developed and delivered security awareness training to 1,000 employees, boosting overall security compliance by 25%.
- •Led security incident investigations, implementing corrective actions that minimized recurrence and documented processes for future use.
- •Reviewed and updated security policies, significantly enhancing compliance with industry best practices and regulatory requirements.
- •Coordinated risk audits and assessments that identified critical vulnerabilities, leading to prioritized remediation efforts.
- •Partnered with the IT department to ensure security compliance is integrated into system development life cycle.
- •Developed documentation for compliance initiatives, improving clarity and accessibility of security policies and protocols.
- •Supported the development and implementation of information security strategies, enhancing compliance by aligning with NIST standards.
- •Conducted security awareness sessions, achieving a 95% participation rate and strengthening the security culture within the organization.
- •Managed third-party vendor security assessments, ensuring compliance with PCI DSS and reducing potential security risks.
- •Generated bi-monthly compliance reports, assisting in streamlined communication with stakeholders and improving organizational transparency.
Data Privacy Analyst resume sample
- •Conducted data privacy audits, resulting in the identification and remediation of over 200 potential vulnerabilities.
- •Collaborated with cross-functional teams to develop an enterprise-wide data privacy strategy, leading to 25% fewer internal policy violations.
- •Implemented training programs on GDPR and CCPA compliance for over 500 employees, enhancing company-wide data privacy awareness.
- •Led incident response efforts for a significant data breach, mitigating further risk and reducing downtime by 15%.
- •Drafted comprehensive data privacy policies and frameworks to align with new legislative updates, successfully passing external audits.
- •Produced regular reports on data privacy metrics that increased transparency and improved customer trust by 20%.
- •Assessed and ensured data handling practices complied with CCPA, leading to a 30% improvement in audit scores.
- •Guided departmental heads on privacy best practices, facilitating seamless cross-department compliance.
- •Monitored data protection legislation updates, and advised management, resulting in timely policy revisions.
- •Co-developed a risk mitigation plan, reducing potential data leakage threats by 40%.
- •Responded to over 100 data subject requests efficiently, ensuring compliance with response time requirements.
- •Developed privacy impact assessments for new projects, identifying risks and ensuring data protection compliance.
- •Resolved privacy-related incidents and data breaches, enhancing response time by 25%.
- •Conducted workshops for over 300 employees, improving understanding of legislative data mandates.
- •Integrated new data mapping processes, increasing accuracy in data storage and retrieval by 35%.
- •Executed baseline assessments of data protection levels, contributing to a 20% risk reduction in data handling.
- •Assisted in developing a compliance framework that met GDPR standards, achieving 100% compliance milestones.
- •Coordinated responses to privacy inquiries, ensuring all responses complied with company policies.
- •Facilitated cross-departmental communication to address and minimize data privacy risks efficiently.
Information Security Audit Specialist resume sample
- •Led a team to conduct over 50 comprehensive security audits per year, improving overall data protection by 25%.
- •Risk assessments executed, leading to a 30% drop in data breaches by proactively mitigating potential vulnerabilities.
- •Documented security policies aligning with ISO 27001, resulting in improved compliance scoring by 40%.
- •Collaborated with IT and security teams on projects, enhancing system security by implementing 10 vital recommendations.
- •Delivered training sessions on security protocols to over 200 staff annually, increasing compliance awareness significantly.
- •Streamlined audit reporting processes, reducing report preparation time by 15% while maintaining detail and accuracy.
- •Managed end-to-end security audits which led to a 20% improvement in regulatory compliance across the company.
- •Worked with external auditors, reducing audit preparation time by 10% through efficient documentation and coordination.
- •Identified critical security gaps in legacy systems and developed remediation plans, averting potential data breaches.
- •Produced detailed audit reports leading to board-level decisions and strategic changes for enhanced security measures.
- •Initiated the adoption of NIST frameworks, which decreased corrective action turnaround times by 35%.
- •Performed detailed risk assessments identifying 40 critical threats and mitigating them to secure sensitive data.
- •Developed and maintained 15 comprehensive risk management procedures, standardizing protocols across departments.
- •Presented complex security findings to a non-technical audience, improving organizational understanding of security risks.
- •Monitored evolving technology trends and updated security policies, which enhanced data integrity by 20%.
- •Executed continuous system security checks resulting in an 18% reduction in identified vulnerabilities year-over-year.
- •Implemented security assessment tools increasing the efficiency of threat detection by 25%.
- •Assisted in the development and deployment of security awareness training for 500 employees, improving threat recognition.
- •Conducted regular reviews of ongoing projects, aligning them with PCI-DSS standards, maintaining high compliance levels.
Information System Forensic Analyst resume sample
- •Led a team that conducted 24 forensic investigations in the past year, improving evidence recovery by 30%.
- •Developed and executed incident response plans, reducing response time by 25% through process optimization.
- •Collaborated with law enforcement on cybercrime investigations, successfully securing convictions in 8 high-profile cases.
- •Overhauled documentation process for forensic procedures, leading to a 40% reduction in report preparation time.
- •Provided expert testimony in 5 court cases, ensuring legal compliance and accuracy of presented digital evidence.
- •Trained 15 staff members on cybersecurity best practices, boosting team productivity and security awareness.
- •Conducted digital forensic analysis for 18 client projects, improving data recovery rate by 45%.
- •Analyzed potential data breaches, preventing over $2 million in potential losses through timely interventions.
- •Evaluated and integrated new forensic tools into existing workflows, resulting in 20% increase in investigation speed.
- •Authored detailed reports and communicated findings, enhancing client understanding and strategic decision-making.
- •Initiated a cross-department training program that revolutionized data security education within the organization.
- •Played a crucial role in building a data breach incident response plan, reducing potential impact by 35%.
- •Managed and preserved data integrity across 15 server environments, securing critical business assets.
- •Led forensic investigations that uncovered $500K in fraud, safeguarding company financial interests effectively.
- •Provided cybersecurity guidance to executive level, influencing company-level decisions regarding security policies.
- •Recovered over 95% of lost data in critical breach incidents, restoring client trust and system operations.
- •Utilized advanced forensic techniques to analyze digital data, identifying security threats in 10 major cases.
- •Collaborated with cross-functional teams to align forensic strategies with company-wide security goals.
Information Security Vulnerability Assessor resume sample
- •Conducted over 100 vulnerability assessments annually, reducing critical vulnerabilities by 95% within the first year.
- •Collaborated with cross-functional teams to implement robust security controls, elevating security posture by 70%.
- •Executed advanced penetration testing techniques on enterprise systems, identifying risks mitigated through dedicated action plans.
- •Led incident response efforts and investigations, shortening response times by 50% across 20 incidents.
- •Enhanced compliance efforts with PCI-DSS and ISO 27001, achieving certification 8 months ahead of schedule.
- •Developed comprehensive documentation of all security assessments and findings, resulting in clearer communication of vulnerabilities.
- •Performed threat modeling and risk analysis for over 200 systems, improving risk management by 60%.
- •Facilitated seamless communication with stakeholders, translating technical vulnerabilities into actionable business insights.
- •Implemented cutting-edge security technologies, reducing overall threats by 75% through proactive threat hunting.
- •Generated weekly reports on security trends and vulnerabilities, improving team readiness by 40%.
- •Assisted in achieving HIPAA compliance by aligning security protocols with industry standards in record time.
- •Advised C-suite executives on cybersecurity strategy, resulting in a 50% decrease in operational security risks.
- •Successfully completed 15 penetration testing projects, identifying key vulnerabilities resolved to enhance security posture.
- •Utilized regulatory frameworks to guide clients through compliance with industry standards quickly and efficiently.
- •Developed customized security solutions, reducing client vulnerability exposure by 55% in under a year.
- •Engineered innovative security solutions, resulting in a 70% increase in application security resilience.
- •Conducted comprehensive security audits, reinforcing vulnerabilities and reducing incidents by 65%.
- •Led successful risk assessments for network infrastructures, influencing strategic improvements.
- •Streamlined IT processes, boosting efficiency by 40% while maintaining high-security standards.
Crafting a standout resume as an information security analyst is like building a robust shield that presents your professional journey with clarity. In your role, you protect vital data, which is crucial, but turning that technical expertise into a compelling narrative on your resume can be challenging. The job market is fiercely competitive, and having a clear and concise resume is crucial for making a memorable impression. Employers are eager to find candidates who not only master complex security systems but can also effectively communicate their skills.
To make this connection, it's important to balance detailing your technical abilities with highlighting your accomplishments. A well-crafted resume not only elevates your profile but also acts as your voice in the job search, illustrating why you're the right fit. Using a resume template can greatly aid in this process by helping you organize your experiences and credentials in a structured way. Resume templates provide a format that ensures your details stand out.
Your resume should clearly convey your success in protecting networks and data systems. When done right, it becomes a powerful tool to advance your career. As you embark on this task, keep in mind that an organized, detailed document is key to making a strong connection with potential employers.
Key Takeaways
- Crafting an effective resume for an information security analyst involves clearly showcasing your technical prowess, achievements, and ability to communicate complex security measures to different audiences.
- It is crucial to use a well-structured template that balances technical skills with personal achievements and can differentiate you from other candidates.
- Highlighting certifications, technical skills, and industry compliance standards in your resume is important to establish your credibility and expertise.
- Quantifying achievements with statistics or clear outcomes provides tangible proof of your impact and expertise in enhancing security measures.
- Including a variety of sections such as education, certifications, skills, and additional personal elements like hobbies or volunteer work can enrich your professional profile and improve resume engagement.
What to focus on when writing your information security analyst resume
Your information security analyst resume should immediately communicate your ability to protect data and manage security risks effectively. Recruiters should quickly grasp your expertise in cybersecurity and understand how your skills have been actively applied to safeguard valuable information.
How to structure your information security analyst resume
- Contact Information: Include your full name, phone number, email address, and LinkedIn profile to make it easy for recruiters to contact you. Ensure your email address is professional, as this sets the tone for your whole application.
- Objective/Summary: Offer a brief, compelling statement to capture recruiters' attention right away—highlight your specific experience in cybersecurity roles. Emphasize impactful skills like threat analysis and risk management, which indicate your direct contributions to previous companies' security efforts.
- Experience: Detail your work history with clear job titles, companies, dates, and responsibilities. Highlight specific achievements such as reducing security breaches or implementing important security updates to demonstrate how your actions have made a tangible difference in past roles.
- Skills: Showcase technical abilities like network security, intrusion detection systems, and incident response techniques to paint a broad picture of your expertise. Including certifications like CISSP or CEH further validates your capabilities, showing you are well-versed in industry standards.
- Education: List your degrees, the institutions where you earned them, and graduation dates. Focus on relevant coursework or projects in information security, which are particularly beneficial to illustrate your academic foundation and practical know-how in the field.
- Certifications and Training: Mention any specialized training or industry certifications you possess to highlight advanced skills that set you apart from other candidates in cybersecurity, showcasing your commitment to maintaining excellence in an ever-evolving landscape.
Transitioning to resume format, below we will cover each section in more depth, making sure your resume aligns with what recruiters are looking for in an information security analyst.
Which resume format to choose
As an information security analyst, presenting your skills and experience with clarity is crucial. Opt for a chronological resume format, which lays out your work history in a straightforward way that tech employers find easy to understand. This approach helps highlight your steady career progression and relevant experience.
Choosing the right font can impact how your resume is perceived, so it's important to pick a modern and professional typeface. Fonts like Rubik, Lato, or Raleway offer a clean and updated look, which can make your resume stand out in a sea of Times New Roman or Arial.
Always save and submit your resume as a PDF, as this filetype preserves your formatting across all devices and platforms. It's crucial when sending your resume electronically to ensure your presentation remains intact.
Standard margins of about one inch on each side allow your content to breathe and maintain a clean layout. This prevents your resume from looking cluttered, making it easier for recruiters to read and focus on your qualifications.
By paying attention to these elements, you'll ensure that your resume not only looks professional but effectively communicates your strengths as an information security analyst.
How to write a quantifiable resume experience section
An information security analyst resume’s experience section should effectively highlight your role in safeguarding data and managing threats. Start with your most recent position to show the progression of your career in the field. Include relevant jobs from the last 10-15 years unless older experiences significantly add value. Tailor your resume for each job application to reflect the specifics of the job ad. Use impactful words such as "enhanced," "implemented," "secured," and "monitored" to describe your actions. Quantify your achievements to illustrate the tangible impact of your work.
- •Slashed security incidents by 45% with advanced monitoring tools.
- •Led a team to craft a cybersecurity framework, boosting protection for 2,000+ users.
- •Conducted security audits, increasing compliance with regulations by 30%.
- •Created a phishing simulation that resulted in a 60% rise in employee alertness.
This experience section effectively demonstrates your proficiency in elevating security measures, shining a light on your role as an information security analyst. Each achievement is quantified, highlighting the significant impact you have had. The use of bullet points neatly organizes these successes, making it simple for employers to grasp your value quickly. The language is tailored to industry standards, ensuring your resume speaks directly to the needs of potential employers, making your contributions stand out as crucial assets.
Growth-Focused resume experience section
A growth-focused information security analyst resume experience section should effectively highlight your ability to enhance security systems and protect against threats. Start by showcasing how your achievements have provided value by reducing security incidents or improving system efficiency, presenting quantifiable successes as evidence of your impact. Each bullet point should start with an action verb that directly communicates your accomplishment, creating a seamless narrative of your contributions.
Share relevant experiences where you've implemented innovative solutions leading to significant improvements. While outlining your responsibilities, focus on key accomplishments, particularly those showcasing growth or pivotal skills. Use numbers or statistics to substantiate your successes, providing solid proof of your expertise. Craft sentences that are straightforward and smoothly interconnected to ensure clear understanding by both humans and automated systems reviewing your resume.
Information Security Analyst
TechSecure Solutions
Jan 2020 - Present
- Led a team of five to overhaul the organization's firewall, which decreased security incidents by 30%.
- Implemented a new intrusion detection system, effectively cutting response time to security threats by 40%.
- Conducted security awareness training sessions that boosted employee compliance with security policies from 65% to 95%.
- Developed a risk management framework that successfully identified vulnerabilities and reduced system downtime by 25%.
Achievement-Focused resume experience section
A strong achievement-focused information security analyst resume experience section should emphasize your contributions and the impact you’ve made effectively. Start by pinpointing specific projects or successes where your involvement was crucial. Highlight how your efforts improved security measures or mitigated risks, using action verbs to give your achievements more impact. Incorporate measurable results such as percentages or time saved to showcase the effectiveness of your actions.
By focusing on these key areas, share how you enhanced protocols, developed systems, and supported organizational goals. Ensure your examples align with the company and role you are targeting, making each bullet point both concise and descriptive. This approach provides clear evidence of your capabilities without overwhelming details, painting a vivid picture of your professional journey.
Information Security Analyst
Tech Solutions Inc.
January 2020 - Present
- Enhanced security protocols, reducing unauthorized access attempts by 30%.
- Implemented a new threat detection system, decreasing response time by 50%.
- Trained staff on cybersecurity awareness, increasing security compliance rates by 20%.
- Developed and tested disaster recovery plans to ensure 100% system availability.
Project-Focused resume experience section
A project-focused information security analyst resume experience section should effectively highlight your skills in managing and delivering security projects. Begin by detailing the projects you've been a part of and your essential role in each one. Use dynamic verbs to describe your actions and highlight their impact on the organization. Each bullet point should focus on specific achievements and ideally include metrics to show the tangible results of your work.
By emphasizing project outcomes, you can clearly demonstrate your impact on enhancing security measures. Highlight how you used your problem-solving abilities to make a difference and underline your effective communication with team members and stakeholders. Focusing on achievements rather than duties helps to illustrate your contributions powerfully. Keep your descriptions concise but provide enough context to make your accomplishments easily understood.
Information Security Analyst
Tech Solutions Inc.
January 2020 - May 2022
- Led a team of five in successfully upgrading the company firewall, significantly reducing network vulnerabilities by 40%.
- Enhanced incident response times through improved cross-department collaboration, achieving a 30% faster resolution rate.
- Crafted and launched a security awareness program, which increased employee adherence to security policies by 60%.
- Conducted security audits and provided insights that bolstered compliance with industry standards by 25%.
Customer-Focused resume experience section
A customer-focused information security analyst resume experience section should highlight your ability to meet customer needs while maintaining security standards. Begin by listing roles where you interacted with customers in security contexts, detailing how you enhanced security measures without compromising trust. Emphasize achievements that demonstrate your skill in balancing customer priorities with security requirements, showing that you can maintain robust security while prioritizing customer needs.
In this section, start each entry with the dates you held the job and your job title, followed by the company's name. Use bullet points to present your achievements and responsibilities clearly. Be specific about what you accomplished, focusing on the skills you applied and the tools or strategies you used. Connect improvements in client satisfaction and response times directly to your security strategies, providing a comprehensive view of your capabilities.
Information Security Analyst
TechSecure Solutions
June 2019 - Present
- Integrated a customer feedback loop into security processes, boosting satisfaction rates by 30% through direct client input.
- Conducted monthly security audits with a team, reducing potential breaches by 40% while ensuring customer usability remained strong.
- Created a transparent customer information portal, which increased client trust and led to higher retention rates.
- Collaborated with cross-functional teams to develop customer-friendly security protocols that enhanced overall user experience.
Write your information security analyst resume summary section
A skills-focused information security analyst resume summary should immediately spotlight your experience and expertise. This section quickly showcases the value you bring to potential employers by highlighting key achievements and skills. If you have significant experience in the field, aim to emphasize your successes and specific talents. Opt for clear and concise language reflecting your professional journey, setting the tone for your entire resume and providing a snapshot of who you are.
For those with substantial experience, consider a summary like this:
This example works well because it cleanly states your years of experience while focusing on key skills like risk management and designing security solutions, which naturally leads to highlighting your leadership abilities and compliance expertise. If you are at the start of your career, a resume objective might be more suitable. While summaries highlight experience, objectives emphasize career goals and how they align with the job. This objective approach targets what you aim to achieve rather than your past work. A resume profile can be a mix of achievements and goals. Alternatively, a summary of qualifications offers a quick list of your skills and accomplishments, giving an overview of your capabilities.
Both the summary and objective provide a snapshot of your skills and career objectives, but the choice depends on your career stage. Tailor these parts to align with job descriptions and company expectations. These initial sections often create the first impression, so clarity and relevance are key to grabbing attention.
Listing your information security analyst skills on your resume
An information security-focused resume should effectively showcase your skills and expertise. Your skills can either stand alone or weave seamlessly into other areas like your experience or summary. Highlighting both strengths and soft skills is crucial because they reveal personal qualities that set you apart. In contrast, hard skills refer to the technical abilities needed for your job, such as software expertise or cybersecurity techniques.
When listing these skills, consider them as essential resume keywords. Recruiters often search for candidates using these terms, so it's important that your skills are both relevant and easily found. Here’s an example of a skills section tailored for an information security analyst role:
This list effectively includes skills directly related to your work, presenting them in a clear and straightforward manner. Each skill highlights a specific area of cybersecurity expertise, demonstrating your well-rounded capabilities.
Best hard skills to feature on your information security analyst resume
Your hard skills are vital to showcase your capability to handle specific tasks and technology. These technical skills highlight your ability to protect systems and data, ensuring you are prepared for the demands of the role. Consider these top in-demand hard skills:
Hard Skills
- Network Security
- Risk Assessment
- Penetration Testing
- Encryption Techniques
- Security Incident Response
- Firewall Configuration
- Malware Analysis
- Data Loss Prevention
- Intrusion Detection Systems
- Cybersecurity Frameworks
- Vulnerability Assessment
- Identity and Access Management
- Cloud Security
- Security Information and Event Management (SIEM)
- Secure Software Development
Best soft skills to feature on your information security analyst resume
Soft skills are equally important as they demonstrate how you interact with others and tackle challenges. For an information security analyst, these skills show your ability to communicate clearly and solve problems effectively. Here are some valuable soft skills to include:
Soft Skills
- Analytical Thinking
- Problem-Solving
- Attention to Detail
- Communication Skills
- Adaptability
- Team Collaboration
- Time Management
- Decision-Making
- Ethical Judgment
- Stress Management
- Creativity
- Conflict Resolution
- Curiosity
- Leadership Qualities
- Empathy
How to include your education on your resume
The education section is a critical part of your information security analyst resume. It shows your academic background and helps demonstrate relevance for the job you're applying for. Tailor this section to include only education relevant to the job. For a degree, write the full title such as "Bachelor of Science in Information Technology." If you have graduated with honors, include distinctions like "cum laude" next to your degree. Including your GPA is optional, but if it's 3.5 or above, consider adding it as it highlights your academic performance. When mentioning GPA, you could use a format like "GPA: 3.8/4.0."
The second example is effective because it includes a degree directly related to information security, making it relevant for an analyst position. The inclusion of a high GPA communicates strong academic performance, while the dates show a realistic timeframe for education in this field. This tailored approach strengthens the connection to the job application and highlights relevant skills and knowledge.
How to include information security analyst certificates on your resume
A certifications section is an important part of an information security analyst's resume. Adding a certifications section can significantly enhance your qualifications and assert your expertise in the field. List the name of each certification clearly. Include the date you obtained each certification. Add the issuing organization's name to validate authenticity. Certificates can also be included in the header to highlight your credentials immediately. For example, "John Doe, CISSP, CEH."
This example is strong because it includes widely recognized certifications relevant to an information security analyst role. Each certification is paired with the issuing body to enhance credibility. The certifications listed demonstrate a commitment to continuous learning and staying updated in the security field. This section helps to build trust with potential employers and sets the stage for further discussions about your expertise.
Extra sections to include on your information security analyst resume
Crafting a well-rounded resume is crucial for your career as an information security analyst. Highlighting different sections in your resume can give potential employers a comprehensive view of your qualifications and personality, making you stand out from other candidates.
- Language section — List languages you speak and indicate your proficiency level. This can demonstrate your ability to communicate with global teams and work in multinational settings.
- Hobbies and interests section — Share a few hobbies that reflect your analytical skills, such as puzzle-solving or gaming. This provides a glimpse into your personality and suggests a balanced work-life approach.
- Volunteer work section — Describe any volunteer activities, especially those tied to cybersecurity or technology. This showcases your commitment to giving back and building real-world experience while supporting community efforts.
- Books section — Mention influential books on security or technology you've read recently. This shows your eagerness to stay informed about industry trends and your dedication to continual learning.
Each of these sections adds depth to your resume and paints a fuller picture of who you are as a professional and individual. By including these elements, you can make your resume more engaging and memorable to potential employers.
In Conclusion
In conclusion, crafting an outstanding resume as an information security analyst involves a strategic blend of showcasing your technical skills, achievements, and personal attributes. Each section of your resume plays a crucial role in painting a complete picture of your professional capabilities and personal interests. By carefully structuring your work experience to highlight quantifiable achievements, you demonstrate the tangible impact of your efforts in previous roles. It is equally important to include a well-rounded skills section, showcasing both the hard and soft skills that are essential in today's information security landscape.
Your education and certifications establish your academic foundation and ongoing commitment to excellence in the field. Including certifications can further validate your proficiency and keep you competitive in this rapidly evolving industry. Beyond technical details, extra sections like language proficiency, hobbies, and volunteer work provide a more comprehensive view of your personality and work ethic, indicating a balanced approach to professional and personal growth.
Choosing the right format, focusing on key achievements, and tailoring your resume for each application add to your chances of standing out in a competitive job market. Whether you are a seasoned expert or new to the field, presenting your qualifications with clarity and enthusiasm captures employers’ attention. Balancing expertise with personal insights ensures that you make a memorable impression, paving the way for career advancement. Emphasizing a combination of strengths throughout your resume reflects your diverse skill set and adaptability, crucial traits in the ever-changing domain of information security.
Related Articles

Continue Reading
Check more recommended readings to get the job of your dreams.
Resume
Resources
Tools
© 2026. All rights reserved.
Made with love by people who care.

